The Importance of Digital Signage Security
Digital signage, with its always-on screens in high-visibility locations, presents an attractive target for cyber attackers aiming to blackmail or embarrass organizations. Over the years, we have witnessed numerous incidents where attackers have taken control of high-profile screens, including those in airports and storefronts. Even if the screens themselves are not the primary target, digital signage players can be exploited as vectors to access other systems.
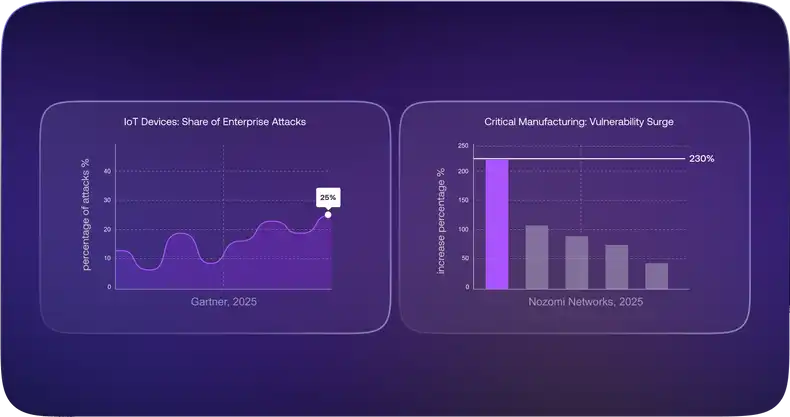
Recent reports highlight the growing cybersecurity risks facing enterprises that fail to secure their IoT devices. According to Gartner, IoT devices are involved in more than 25% of enterprise attacks. Moreover, outdated and End of Life (EoL) devices and operating systems are frequently deployed, creating significant security vulnerabilities as they often lack the latest security patches and updates (Nozomi Networks). Asimily’s report underscores that routers and digital signage systems are among the most targeted IoT devices due to their frequent use and often inadequate security measures (Asimily).
Key Cybersecurity Statistics
- Gartner: IoT devices are involved in over 25% of enterprise attacks (Gartner).
- Asimily: A significant number of IoT attacks exploit legacy vulnerabilities, with routers and digital signage systems being prime targets (Asimily).
- Nozomi Networks: Network anomalies and attacks are prevalent in OT and IoT environments, with critical manufacturing vulnerabilities surging 230% (Nozomi Networks).
No one wants to start their day explaining a digital signage hack to their boss. Worse yet is having to explain how this system was used to launch a ransomware attack that holds company data hostage. This is why banks, hospitals, and other security-focused organizations trust Screenly.
Screenly’s Commitment to Security
Security is ingrained in Screenly’s DNA. Our founders come from the cybersecurity industry, and since our inception, security has been our top priority, not just a marketing term.
Security Measures in Our Digital Signage Players
Our digital signage players are designed with multiple layers of security to thwart potential attacks. Here’s a detailed look at our security technologies:
Process Isolation
We utilize advanced Linux Kernel technologies such as namespaces, cgroups, AppArmor, and Seccomp for robust process isolation. This prevents lateral movement even if part of the player is compromised. Unlike competitors, our approach restricts runtime users from executing system commands or installing tools, significantly raising the bar for attackers.
Transactional and Cryptographically Signed Updates
To counter rogue updates, we employ cryptographically signed updates. Our players reject any update that fails cryptographic verification, ensuring only legitimate updates are applied.
Full Lockdown
By eliminating open ports, we prevent remote access vulnerabilities, a common attack vector for IoT devices. This measure is increasingly important with the adoption of IPv6. Unlike competitors with default-enabled SSH and default credentials, our players assume public accessibility and are designed accordingly.
No Default Credentials
Screenly players do not use default credentials or backdoors for convenience, addressing a significant security risk and complying with legislation such as the EU’s Cybersecurity Act (Regulation (EU) 2019/881) and the US’s IoT Cybersecurity Improvement Act of 2020 (H.R. 1668).
Automatic Security Updates
Our players automatically apply security updates without interrupting content playback. Both OS and software updates are transactional and cryptographically signed.
Full Encryption for All Traffic
All communication between our players and backend is fully encrypted, preventing MiTM attacks. We use Mutual TLS (mTLS), with client private keys securely stored in the TPM on eligible players.
Automatic Security Scans
We conduct regular security audits on third-party dependencies to maintain a secure environment.
End of Life Management
Screenly publicly states the End of Life (EoL) cycles of our operating system software. We provide mitigation strategies for scenarios where automatic remote updates are not feasible, ensuring devices remain secure even as software reaches its EoL stage.
For more technical details, refer to Ubuntu Core’s security whitepaper.

Security of Our Back-End and Web Interface
Our cloud component is equally secured with the following measures:
Process Isolation
Similar to our players, we use Linux Kernel level process isolation to limit attack potential.
Automatic Vulnerability Scanning
We continuously scan our runtime environment for vulnerabilities, covering both application dependencies and container vulnerabilities.
Ephemeral Infrastructure
We use short-lived servers that are replaced every 24 hours, ensuring they are always patched against recent vulnerabilities.
Additionally, our web interface is designed to secure user accounts with features such as:
Two-Factor Authentication (2FA)
We support TOTP-based 2FA and are planning to add hardware token support.
Granular Access Control
Define specific access levels for each team members to ensure they adhere to the principle of least privilege (PoLP.)
Team-Based Screen Management
Create multiple teams with defined member permissions to further isolate access.
We are committed to continuously enhancing our security features. For any questions or concerns, please reach out to Screenly Support.



